I. A Strawman Proposal
a. Basic password system: file w/ username, password records (colon delimiter)
b. Simple to implement but risky
- All users compromised if hacker get the password file
- Done in Java: MiniPasswordManager
c. MiniPasswordManager
Public class MiniPasswordManager {
/** dUserMap is a Hashtable keyed by username */
private static Hashtable dUserMap;
/** location of the password file on disk */
private static String dPwdFile;
public static void add (String username, String password) throws Exception {
dUserMap.put(username, password);
}
Public static Boolean checkPassword(String username, String password) {
try { String t = (String) dUserMap.get(username);
return (t == null) ? false: t.equals(password);
} catch (Exception e) {}
return false;
}
…
}
d. MPM: File Management
public class MiniPasswordManager {
…
/* Password file management operations follow */
public static void init (String pwdFile) throws Exception {
dUserMap = MiniPasswordFile.load(pwdFile);
dPwdFile = pwdFile;
}
public static void flush() throws Exception {
MiniPasswordFile.store (dPwdFile, dUserMap);
}
… // main()
}
e. MPM: main()
Public static void main(String argv[]) {
String pwdFile = null;
String username = null;
try {
pwdFile = argv[0];
username = argv[1];
init(pwdFile);
System.out.print(“Enter new password for “ + username + “: “);
BufferedReader br = new BufferedReader (new InputStreamReader(System.in));
String password = br.readLine();
add(username, password);
flush();
} catch (Exception e) {
If ((pwdFile != null) && (username != null)) {
System.err.println(“Error: Could not read or write “ + pwdFile);
} else { System.err.println(“Usage: java MinipasswordManager” + “<pwdfile> <username>”); }
}
}
II. Hashing
a. Encrypt passwords, don’t store “in the clear”
- Could decrypt (e.g DES) to check, key storage
- Even better: “one-way encryption”, no way to decrypt
- If file stolen, passwords not compromised
- Use one-way hash function, h: preimage resistant
- Ex: SHA-256 hashes stored in file, not plaintext password
b. Hashing Example
a. Basic password system: file w/ username, password records (colon delimiter)
b. Simple to implement but risky
- All users compromised if hacker get the password file
- Done in Java: MiniPasswordManager
c. MiniPasswordManager
Public class MiniPasswordManager {
/** dUserMap is a Hashtable keyed by username */
private static Hashtable dUserMap;
/** location of the password file on disk */
private static String dPwdFile;
public static void add (String username, String password) throws Exception {
dUserMap.put(username, password);
}
Public static Boolean checkPassword(String username, String password) {
try { String t = (String) dUserMap.get(username);
return (t == null) ? false: t.equals(password);
} catch (Exception e) {}
return false;
}
…
}
d. MPM: File Management
public class MiniPasswordManager {
…
/* Password file management operations follow */
public static void init (String pwdFile) throws Exception {
dUserMap = MiniPasswordFile.load(pwdFile);
dPwdFile = pwdFile;
}
public static void flush() throws Exception {
MiniPasswordFile.store (dPwdFile, dUserMap);
}
… // main()
}
e. MPM: main()
Public static void main(String argv[]) {
String pwdFile = null;
String username = null;
try {
pwdFile = argv[0];
username = argv[1];
init(pwdFile);
System.out.print(“Enter new password for “ + username + “: “);
BufferedReader br = new BufferedReader (new InputStreamReader(System.in));
String password = br.readLine();
add(username, password);
flush();
} catch (Exception e) {
If ((pwdFile != null) && (username != null)) {
System.err.println(“Error: Could not read or write “ + pwdFile);
} else { System.err.println(“Usage: java MinipasswordManager” + “<pwdfile> <username>”); }
}
}
II. Hashing
a. Encrypt passwords, don’t store “in the clear”
- Could decrypt (e.g DES) to check, key storage
- Even better: “one-way encryption”, no way to decrypt
- If file stolen, passwords not compromised
- Use one-way hash function, h: preimage resistant
- Ex: SHA-256 hashes stored in file, not plaintext password
b. Hashing Example
c. Hashing MPM Modifications
public static void add (String username, String password) throws Exception {
dUserMap.put(username, computeSHA(password));
}
public static Boolean checkPassword(String username, String password) {
try { String t = (String) dUserMap.get(username);
return (t == null)?false:t.equals(computeSHA(password));
} catch (Exception e) {}
return false;
}
private static String computeSHA (String preimage) throws Exception {
MessageDigest md = MessageDigest.getInstance(“SHA-256”);
md.update(preimage.getBytes(“UTF-8));
byte raw[] = md.digest();
return (new sun.misc.BASE64Encoder().encode(raw));
}
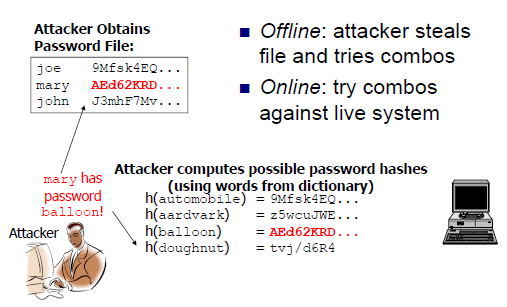
III. Off-line Dictionary Attacks
IV. Salting
a. Salting – include additional info in hash
b. Add third field to file storing random #(salt)
c. Salting Functions
public static int chooseNewSalt() throws NoSuchAlgorithmException {
return getSecureRandom((int)Math.pow(2,12));
}
/* Returns a cryptographically random number in the range [0, max) */
private static int getSecureRandom(int max) throws NoSuchAlgorithmException {
SecureRandom sr = SecureRandom.getInstance(“SHA1PRNG”);
Return Math.abs(sr.nextInt())%max;
}
public static String getSaltedHash (String pwd, int salt) throws Exception {
return computeSHA(pwd + “|” + salt);
}
d. Salting in MPM
/* Chooses a salt for the user, computes the salted hash of the user’s password, and adds a new entry into the userMap hashtable for the user */
public static void add(String username, String password) throws Exception {
int salt = chooseNewSalt();
HashedPasswordTuple ur = new HashedPasswordTuple(getSaltedHash(password, salt), salt);’
dUserMap.put(username, ur);
}
public static Boolean checkPassword(String username, String password) {
try { HashedPasswordTuple t = (HashedPasswordTuple) dUserMap.get(username);
return (t== null)?false: t.getHashedPassword().equals(getSaltedHash(password, t.getSalt()));
} catch (Exception e) {}
return false;
}
e. Salting: Good News
- Dictionary attack against arbitrary user is harder
- N-word dictionary, k-bit salts, v distinct salts
- Off-line Dictionary Attack Foiled
g. Salting: Bad News
- Ineffective against chosen-victim attack
- Attacker’s job harder, not impossible



Δεν υπάρχουν σχόλια:
Δημοσίευση σχολίου